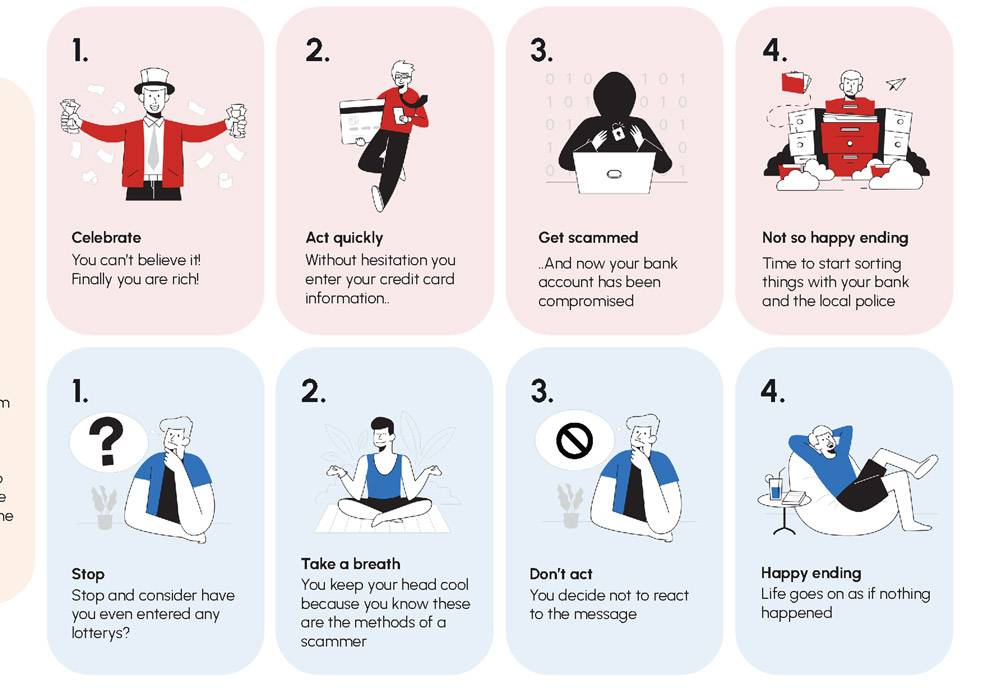
Introduction to Phishing
Phishing is a form of social engineering. Unlike other cyberattacks that directly target networks and resources, social engineering attacks use human error, fake stories, and pressure tactics to manipulate victims into unintentionally harming themselves or their organisations. In a typical phishing attempt, a criminal pretends to be someone the victim trusts, such as a colleague, boss, authority figure, or representative of a well-known brand. The criminal sends a message instructing the victim to pay an invoice, open an attachment, click a link, or take some other action.
The evolution and impact of phishing attacks
Phishing, a term now synonymous with cybercrime, originated from a program developed by a teenager in Pennsylvania called AOHell. This early malware targeted AOL (America Online), a popular online service in the early days of the internet, using mechanisms to steal credit card information and crack passwords, leading to disruptions in AOL’s services. The AOHell program laid the groundwork for automated phishing software, influencing subsequent phishing methods, including those used by the Warez community – a group involved in hacking and sharing pirated software.
The early days of phishing
The Warez community is credited with the first organised phishing attacks, which began in 1996. They targeted AOL users by using an algorithm to generate random credit card numbers. When they found a valid number, they created real AOL accounts to scam other users. This initial phishing scheme evolved into more sophisticated social engineering tactics, with attackers impersonating AOL employees to collect sensitive information.
Following these early scams, phishing tactics rapidly transitioned to email. Early phishing emails ranged from unconvincing schemes, such as those involving fake Nigerian princes, to more sophisticated attempts like the Mimail virus of 2003. The Mimail virus was distributed through an email that claimed to be from PayPal, urging users to update their credit card details. Many users, misled by the convincing PayPal logo, entered their credentials on a malicious website.
The human-centric threat
Phishing is particularly dangerous because it exploits human psychology rather than relying on technological vulnerabilities. Attackers often do not need to breach systems directly or outsmart cybersecurity tools. Instead, they deceive individuals with authorised access to sensitive information, leading them to unwittingly assist in the attack.
Phishers can range from individual scammers to organised criminal gangs and can use phishing for various malicious purposes, including identity theft, credit card fraud, money theft, extortion, account takeover, and espionage. Targets of phishing attacks include individuals, corporations, and government agencies. One notable example is the phishing attack on Hillary Clinton’s 2016 US presidential campaign, where Russian hackers used a fake password-reset email to steal thousands of emails. Even the campaign’s IT help desk was fooled by the fraudulent emails.
Modern phishing techniques
Phishing has evolved significantly, utilising multiple communication methods and sophisticated techniques to deceive targets. Modern phishing attempts can closely mimic legitimate companies, making it challenging to detect them without careful scrutiny.
Some contemporary phishing techniques include:
- Angler Phishing: This occurs via social media, using spoofed URLs, instant messages, or fake profiles to gather sensitive information. Attackers may also exploit social media profiles for personal information to enhance their manipulation.
- Cloning and Domain Spoofing: Attackers create emails that closely resemble legitimate ones, using exact copies of messages or forging domain names to make emails appear genuine. They often impersonate large, well-known companies to trick users into divulging personal information.
- Smishing: This technique combines phishing with SMS, sending fake text messages to collect information such as credit card numbers or passwords.
- Spear Phishing: Highly targeted, spear phishing involves attackers gathering detailed information to craft personalised emails that appear to come from trusted sources.
- Whaling: This type of phishing targets senior-level employees or high-profile individuals, often involving sophisticated social manipulation and intelligence gathering.
- Vishing: Combining phishing with VoIP (voice over Internet Protocol), vishing involves fraudulent phone calls aimed at obtaining sensitive information.
In summary, phishing has evolved from early programs like AOHell to complex schemes involving various communication methods. The threat remains significant because it preys on human psychology, making it essential for individuals and organisations to remain vigilant and informed about these ever-evolving tactics.
If you want to learn more about this topic, check these:
https://www.ibm.com/topics/phishing